Operating system: Windows, Android, macOS
Group of programs: Business automation
Control of visits
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
Program screenshot
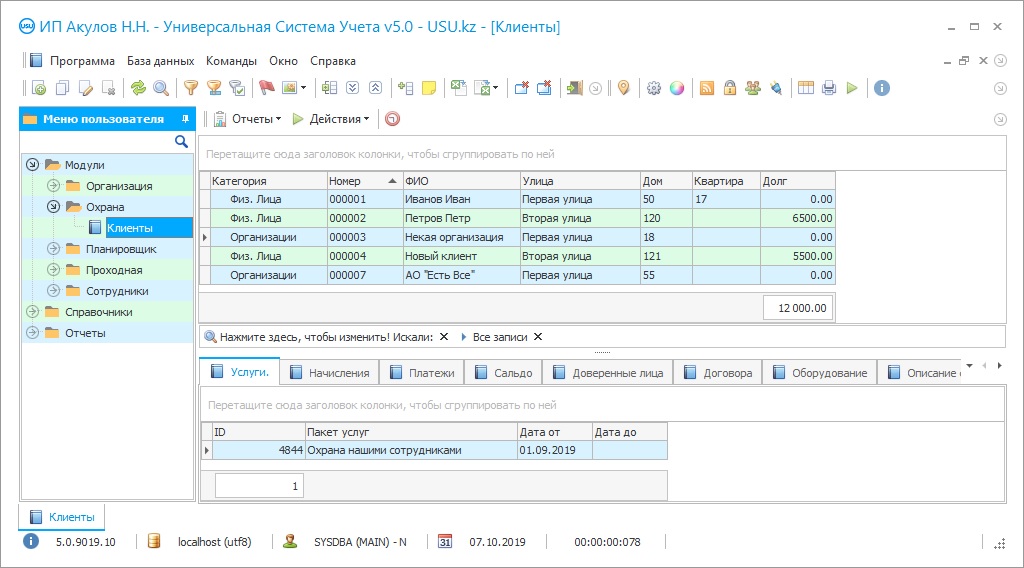
The control of visits is carried out by security personnel and is one of the main measures taken by the company to maintain the safety and control of personnel. Control of visits is carried out most often at the internal entrance of a separate enterprise or an entire business center and implies the registration of each visitor in special accounting documents or a digital system. Since there are two categories of visitors, temporary visitors, and staff members, the approach to their registration is different. And if some simply fix their arrival at the workplace, others are obliged to indicate the purpose of their visit. In order for the internal control of visits to be carried out effectively, it is necessary to provide security personnel with all the necessary tools. In many ways, their availability and practicality depend on the chosen method of monitoring visits, which might be manual or automated. Despite the fact that manual control has been a popular procedure for many years, this approach to management is obsolete and does not allow processing information flows arriving at a huge speed quickly and efficiently. Automation makes it possible to get rid of the dependence of the quality of accounting on the human factor by replacing personnel in performing a number of daily functions with artificial intelligence of specialized software. The automated method of managing processes at the checkpoint qualitatively changes the result of control and the process of obtaining it. Thanks to automation, fast and high-quality data processing is continuously carried out in the electronic database, without any mistakes and errors. Conducting control in electronic format allows you to achieve the security and safety of information, which is extremely important in the modern world. Automated control of visits implies the ability to display related statistics, which allows for more effective control of personnel. In order to automate a security company or a separate security department, it is necessary to install specialized software, the options of which are now great, and all thanks to the active development of this direction in the modern world of technology. Among them, there are different samples, both in terms of pricing policy and the proposed functionality, so you’re able to easily choose a sample suitable for your organization.
One of these options for software installations that have the necessary potential for monitoring visits and other automation capabilities is the USU Software. Created by the USU Software development team’s specialists more than eight years ago, it is filled with their many years of knowledge and experience. USU Software is a licensed application that regularly updates its features in accordance with the latest automation techniques through the installation of updates. It helps to establish internal accounting in the company in many of its aspects, making management easy and comfortable. Before installing this advanced system, you’ll go through an online consultation with our specialists in order to select a configuration suitable for your business, of which there are more than twenty types. This was done taking into account the fact that each type of activity needs its own set of options for high-quality management, so the program is considered to be universal. You’re able to install and configure the application remotely, which is very convenient if you have decided to cooperate with our company from another city or even country. To do this, you just need to connect the computer on which Windows operating system is installed to the Internet and provide access to it for our programmers. It is quite easy to master the unique computer software, even on your own. Unlike competing programs, you do not need to spend time and money on additional training. It will be possible to understand the structure of the program using free training videos posted on the official website of the USU Software, and the hints built into the interface greatly facilitates the conduct of activities in the application for the first time. An unlimited number of people can simultaneously exercise internal control of visits, who, for efficient decision-making, can also exchange messages and files directly from the system interface. This won’t be difficult due to the fact that the software installation is easily integrated with such communication resources as SMS, e-mail, mobile messengers, Internet sites, and even a telephony station. Also, it is worth mentioning that the automated application is able to synchronize and automatically exchange data with various modern devices that can be used in the course of industrial security activities. These include hardware such as a bar code scanner, which is usually built into a turnstile, a web camera, CCTV cameras, and other devices.
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-05-12
Video of control of visits
This video can be viewed with subtitles in your own language.
For the internal control of staff visits to the workplace, the main thing is that at the entrance each employee is registered in the system installation. For this, both a login and password for entering a personal account can be used, as well as a special badge equipped with a unique bar code, which is used much more often in everyday life. The bar code management helps to quickly identify the employee in the electronic database since the code is attached to his electronic contact card. For temporary visitors, a different algorithm is used. In order to register their visit, the security officers manually create a temporary pass for them, in which all the necessary information is entered, including the purpose of the visit. In order for the pass to be most useful, a photograph of the visitor is printed on it, taken at the checkpoint on a webcam. Thus, each category of visitors is recorded in the internal accounting and you will always have the opportunity to view their statistics in the ‘Reports’ section of the program. There you can also identify overtime or violations of staff compliance with the work schedule, which can be taken into account when automatically calculating wages. By organizing the control of visits in this way, the safety of your enterprise can be guaranteed, and data about visitors is stored for a long time, in case of conflict production situations.
So, summing up the material of the essay, I would like to say that automation with the help of the USU Software is the best tool in the course of professional and effective management of the security service. Test its capabilities completely free of charge using the test demo version within your company and make the right decision when purchasing it. Any number of employees of the organization can be involved in monitoring visits, provided that they are connected by a single local network or via the Internet. It is especially important to control visits at the entrance of the business center, which is easily accomplished using the digital security system.
Download demo version
Thanks to the analytical abilities of the ‘Reports’ section, you’ll be able to view the statistics of the purpose of the visits of temporary visitors. Internal control of visits contributes to the correct filling of the electronic time-sheet for employees of the organization, taking into account all overwork and hours that are needed to be worked. All information on visits to your enterprise should be stored in the electronic database for as long as you need.
The beauty of tracking visits digitally is that the data is always available for viewing. In an automated application, it is very convenient to monitor the shift schedule of security personnel, and, if necessary, swap them without any difficulty. It is also convenient to keep track of the purchase and provision of services for the installation of alarms and other security sensors in the program. The same personnel database, formed in computer software, can be used in the activities of the company for different purposes. Thanks to the communicative capabilities of the software installation, you can promptly notify a colleague that a visitor has come to him. To form a calculation for the clients of your organization, a flexible tariff scale can be used.
Order a control of visits
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

The program will be installed
If the program is purchased for 1 user, it will take no more than 1 hourBuy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!
Control of visits
This advanced program can conduct a separate control over existing contracts and their validity periods, where those coming to the end of the contract are displayed for your convenience in a separate list. Synchronizing internal and external financial payments help to cleverly assess the financial situation in the company. In the course of the activity, mass charges of subscription fees can be applied for a one-time settlement with all customers. USU Software can keep an internal record of authorized persons for each customer, for which all the necessary documentation is scanned and saved. Support for automatic generation and printing of internal documentation necessary for the work, according to prepared templates.









