Operating system: Windows, Android, macOS
Group of programs: Business automation
Spreadsheet for a checkpoint
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
Program screenshot
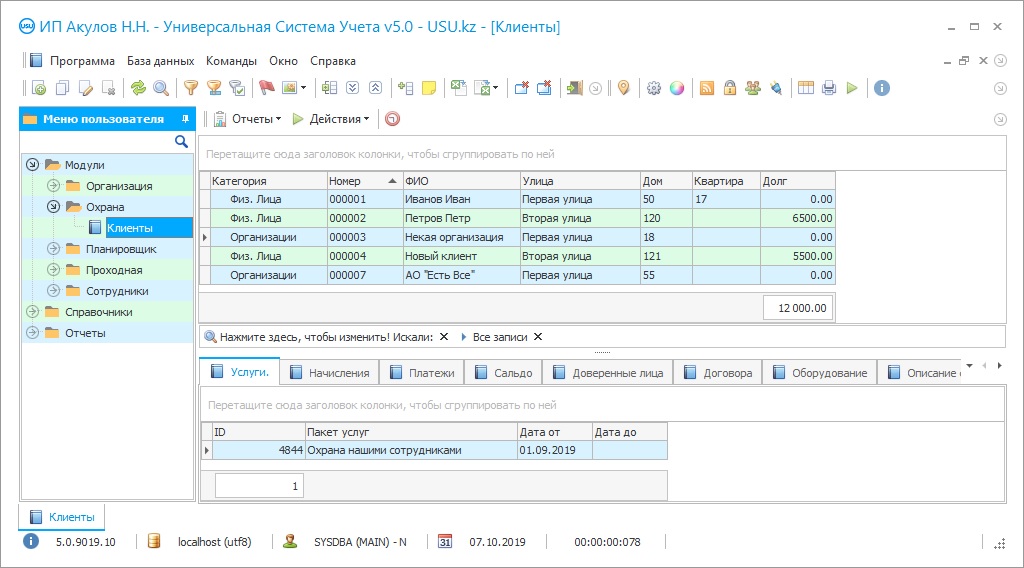
The checkpoint spreadsheet is used at the entrance to any building, office, and enterprise is a mandatory and necessary procedure. When registering, a rectangular blue magazine is usually used, in which lines and names are manually drawn, and a simple gel pen. Clients spend a few minutes filling out their visit details, and it’s good if he doesn’t forget to bring his identification documents with him. Otherwise, the checkpoint either be difficult or unnecessary red tape created. In our high-tech modern times, scientific progress has gone beyond paperwork. They were replaced by digital technologies and programs, like passing through a people spreadsheet. The development team of the USU Software system has created such a checkpoint tool that saves you time, speeds up the process of actions, and optimizes the entire work cycle. If you are wondering ‘How?’, then just read on. To explore the possibilities of a checkpoint spreadsheet, you can download a free trial. Downloading a checkpoint spreadsheet is an easy and simple process, after the execution of which you receive a shortcut on your desktop. Having opened it, you need to enter your user logins and passwords, which are protected by your arbitrary codes. As a leader, you can see the actions and work of all your employees, analytical and financial calculations, income and expenses, and much more. But an ordinary employee of your organization does not see his grips anymore, and you may be calm about the solidity and security of papers and company discharges. Having entered the application, a window with the USU Software emblem opens in front of you. In the overhead left corner, you will notice a list of the basic three sections. These are ‘Modules’, ‘References’ and ‘Reports’. All routine activities are carried out in ‘Modules’. Opening the top section, you will see subdivisions such as ‘Organization’, ‘Security’, ‘Planner’, ‘Checkpoint’, and ‘Employees’. If we briefly dwell on the subsections to go to the subsection of interest to us, the Passage, then it takes after this. So, the ‘Organization’ has all the information about the operations of the company, for example, about products and money. The ‘Guard’ has data on the users of the security agency. The ‘Planner’ helps you not to forget about proceeding events and arrangements, also saving statistic bulk in the database, and the ‘Employees’ concentrate information about the presence of every working individual, his late arrivals and working hours. Finally, the ‘Gateway’ contains all shreds of evidence about existing ‘Organizations’ in the building and ‘Visits’ by clients and others. The checkpoint spreadsheet is informative and understandable. The date and season of visits, the second name, and surname of the visitor, the name of the company to which he came, the number of the validation card, a chit, and the administrator or guard who added this notation, are automatically inputted into it. Our advanced visitor registration spreadsheet also includes a digital signature. By ticking the receptacle, the man who added the visitor takes input data responsibility. Another advantage of the registration tool is the ability to download a photo and scan a document. Practical functionality, user-friendly interface, and quick commands help to significantly facilitate the mechanism of protection and security. On supreme of all this, not only the enrollment of visitors but also the monitor of the personnel within your control. Indeed, in the ‘Employees’ subsection, you may see all the info about what season the worker came, when he left, and how much he operated productively. Also, in the ‘Reports’, after you have downloaded the spreadsheet, you may easily draw up analytical reports and graphs, visual diagrams. This was a rapid introduction to the spreadsheet capabilities, however, note that in an annex to the above, our managers may come up with other options by providing a complete product.
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-05-14
Video of spreadsheet for a checkpoint
This video can be viewed with subtitles in your own language.
The checkpoint table in the information tool has a single client base of the organization, which speeds up the notification process in the event of some changes, cash control, and quick search. When working with security using our information tool, it is possible to divide the agency's clients into the necessary categories and download general data. The database mechanically saves all phone numbers, places, and details, which noticeably accelerates the workflow. In our security system, you can register any number of services and download all the information by pressing one button. Handy search by service title, category, the customer also optimizes the aggregate workflow and workload of the enterprise's employees. Using the work of a security firm's information system, payment accepted both in cash, that is, in money, or by bank transfer, using cards and download transfers. Here you can also monitor the score of prepayment and obligations. With the aid of our information instrument, you can dissect the income and expenses of your company without unnecessary red tape and headaches. When verifying the reports of the organization, it is possible to picturize the data with graphs, charts, and a visual spreadsheet. You should download the trial version on our website for free.
Download demo version
USU Software proposes a derivation assay of advertising performance and other charges using your database. The work of the guard involves working with clients, and thus communication with them by calls and messages. To simplify this goal, you can use the option of robot calls to the client base. Also, you gain a notification about the condition of the order, credits, deadlines, and branches, which belittles the influence of the human factor on the benefit and the prestige of the enterprise. With the aid of the announcement properties of the working tool, you do not forget to make a payment or, on the contrary, demand debts from clients, download the necessary information into or from the checkpoint system. One of the functions of the checkpoint spreadsheet system for working with security agencies automatically translate your audio recordings into text messages. A security spreadsheet system also does much more!
Order a spreadsheet for a checkpoint
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

The program will be installed
If the program is purchased for 1 user, it will take no more than 1 hourBuy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!









