Operating system: Windows, Android, macOS
Group of programs: Business automation
Control of checkpoint
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
Program screenshot
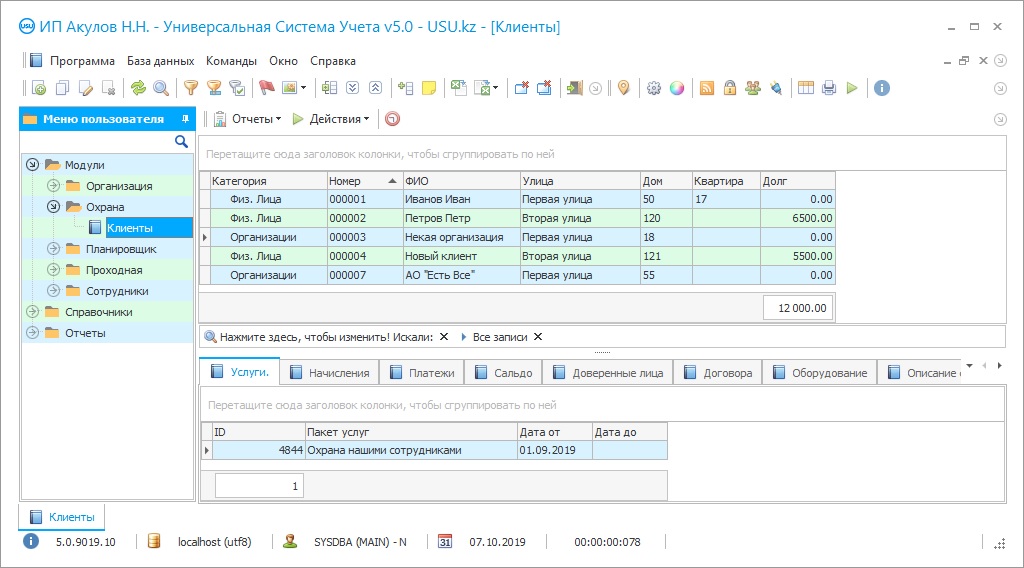
Control of the checkpoint at any enterprise involves the solution of a certain list of tasks related to the organization and observance of the checkpoint scheduling. The number and types of tasks may vary depending on the type of organization, it might be manufacturing, trading enterprise, government agency, or a lot more. The checkpoint is designed to protect the interests of the enterprise through the development and strict observance of a set of measures and rules that determine the procedure for access to the protected area, and exit from it, for company employees, visitors, vehicles, and material values. As a rule, these measures and rules are a combination of various, prohibitions, permissions, restrictions, and so on, which often do not find understanding and approval on the part of those who fall under them. Therefore, strict observance of the legislation is of particular importance here, so as not to create unnecessary problems for the organization. Obviously, access control at the checkpoint for people should be noticeably different from the control and inspection of vehicles, especially with a load of inventory items. Accordingly, different requirements are imposed on the technical and organizational support of the checkpoints for people and transport. In particular, this concerns the use of modern technical devices, namely electronic turnstiles, gates, access card readers, gate gates, bar code scanners, CCTV cameras, and so on. But in any case, a special checkpoint control program is not a luxury, but an urgent need to ensure that the work is carried out as efficiently as possible and the functions are performed in full.
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-05-15
Video of control of checkpoint
This video can be viewed with subtitles in your own language.
USU Software offers its own unique IT development, which provides not only proper control of security at the checkpoint but also optimization of all processes related to protecting the interests of the enterprise and ensuring the safety of its resources. An electronic checkpoint is an economically optimal solution that restricts access to the protected area, as well as contributes to monitoring compliance with work discipline, for example, late arrivals, overtime, smoke breaks, and so on, creating a common database of visitors. Internal control of the checkpoint is carried out from a single control panel by the officer on duty. It also displays alarm signals, video cameras, perimeter sensors, and other technical devices integrated into the program. The built-in map allows you to quickly determine the location of any security officer, as well as quickly localize events and incidents at the security facility, and send the nearest patrol to the site. The program can work in one or several languages, according to the customer's choice. An advanced built-in scheduler provides the ability to assign work plans for each object separately, program the parameters of automatically generated summary reports, backup deadlines, and a lot more.
Download demo version
USU Software assists in the control and registration of visitors to the protected area, creating a specialized database that allows you to analyze the dynamics of visits by days of the week, duration, purpose of visits, company employees, and so on, print permanent and one-time passes with a photograph of the visitor right on the spot. Management summary reports provide the security management with the opportunity to monitor each employee, calculate piecework wages and material incentives, assess the level of effectiveness of measures to protect the interests of the enterprise, analyze incidents and develop methods of prevention and urgent elimination of consequences, and a lot more.
Order a control of checkpoint
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

The program will be installed
If the program is purchased for 1 user, it will take no more than 1 hourBuy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!
Control of checkpoint
The checkpoint control program ensures the streamlining and optimization of all related business processes. This professional level of software development meets international standards and the highest customer requirements. An electronic checkpoint installed within the USU Software guarantees optimal access control for people and vehicles. System settings are made on an individual basis, taking into account the characteristics and specifics of the customer and the objects of protection. Access control to the territory of the facility is carried out using electronic control and tracking. USU Software works with an unlimited number of control points, you can organize as many checkpoints as required for optimal operation of the enterprise. Checkpoint control of the application can be equally effectively used in manufacturing and trade enterprises, service companies, business centers, government agencies, and so on.
An electronic checkpoint streamlines the accounting of performance indicators of employees of the enterprise, recording delays, overtime, movements during the working day, etc. The control of access to the territory of the protected object for persons who are not employees of the company is equally effective. The database contains a complete history of all visits, including the date, time, and purpose of the visit, the length of stay in the territory, car numbers, the receiving employee, and other information. One-time and permanent passes with the attachment of photos can be printed directly at the entrance.
An unlimited number of different types of technical devices, such as cameras, locks, turnstiles, fire alarms, navigators, motion sensors, and many more are used by the security service to solve work tasks can be integrated into this program. Built-in scheduling tools allow you to create general plans for the protection of facilities, individual plans, and schedules for each employee, the schedule of duty shifts, optimal routes to bypass the territory, and so on. If necessary, the program has a mobile version for both employees and clients of the company that helps to increase the closeness and efficiency of interaction between the two.









