Operating system: Windows, Android, macOS
Group of programs: Business automation
Facilities protection management
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
Program screenshot
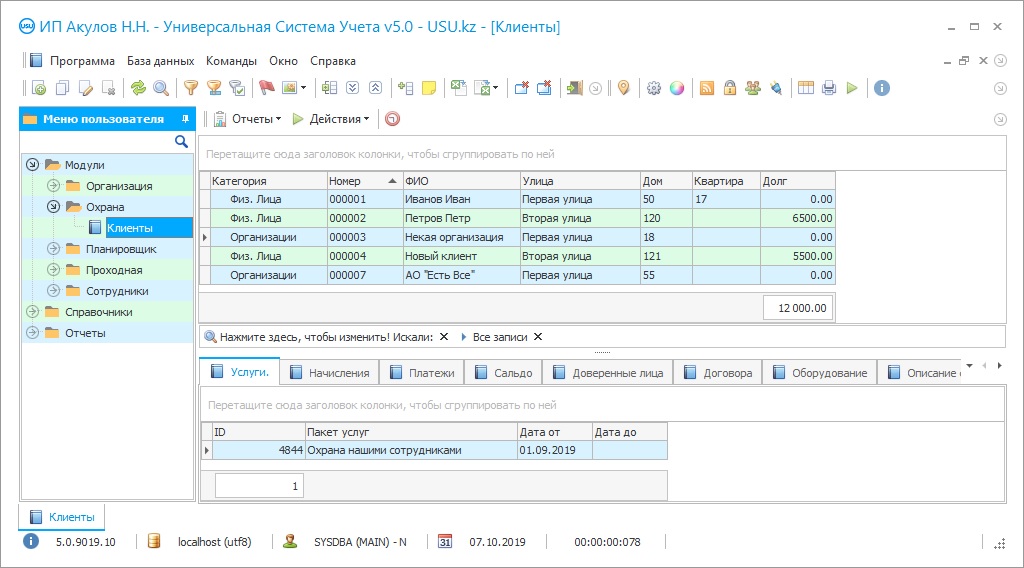
The management of the protection of objects is carried out in close connection with the fact that the protected object is. There are organizations and facilities that are protected in a special regime. Usually, these are state facilities, scientific associations, military facilities, organizations in the work of which there is a state secret. There are firms and companies whose activities are not classified as secret. But they also try to ensure high-quality protection of their trade secrets and intellectual property.
The protection of an object, regardless of its type, must continuously ensure the safety of the organization, management visits, and checkpoints, prevent unauthorized access to the territory of the object, take into account incoming vehicles and cars that leave the territory. In addition to this activity, the protection of the facility always includes inspections and patrolling, management of premises, alarms, and a panic button.
The correct management of these processes is based on two important principles. The first is planning. Each employee on the site must clearly understand their responsibilities and tasks. The second is management. It is needed at every stage of activity, for every action of the guard. Only if both principles are observed can we say that the management was not mistaken with the protection management at this facility.
So, we have an object of protection and a staff of people for this. How to approach management correctly? Firstly, take into account all the nuances of the facility, familiarize yourself with the plans of exits and entrances, the perimeter, and the specifics of the activity. Then you should start drawing up a plan — establishing guard posts at the most problematic points, distributing responsibilities between them, drawing up instructions for each post. And then the fun begins — business management and management.
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-05-10
Video of facilities protection management
This video can be viewed with subtitles in your own language.
Here you can use the experience of other similar companies — instruct the guard to keep written records of every action taken within the framework of the instruction. For example, an employee at the entrance checks passes keeps a log of visits. An employee on the territory of the warehouse manages the export of goods and the import of raw materials and materials, making notes in the appropriate journal. The group patrolling the area will keep a log of the patrol report and so on.
There is no doubt that the guards will not sit without work. Most of the time will be spent on drawing up various reports. And now let's imagine that an emergency happened at the facility, it is urgently required to find data on incoming and outgoing for a certain date or period, on transport. Here you’ll have to try because there are a lot of accounting journals, and there is always a possibility that the protection has forgotten to enter some data.
Managing the manual way is hampered by the influence of the human factor. It concerns staff fatigue, forgetfulness. One cannot fail to mention the likelihood of deliberate distortion of information in the reports under the influence of bribes, blackmail, or threats. Will an object guarded in this way be completely safe? Unlikely. A more modern method, taking into account all the listed principles of good management, was proposed by our development team — the USU Software. She has developed a program that will completely solve management problems in the protection of objects. It’ll facilitate planning, automate document flow and reporting, help maintain continuous and constant management over activities, minimize the impact of the human factor, reducing the likelihood of corruption-related events.
Protection personnel should be exempted from compiling paper logbooks. Management of visitors, transport, work shifts, and shift records will be kept by software. The time freed from paperwork, protection guards can use to perform their basic professional duties, increasing the degree of protection of the entrusted object. The boss will be able to see automatically generated reports on all performance indicators and for each employee in particular. This provides the best possible management. The program automates the entrance regime and management of admissions, reducing the likelihood of corruption because the attacker will not be able to agree with the program, it is not afraid and does not take bribes. In addition to protecting the facility, the system will be useful to all other departments of the facility — it’ll help the accounting department to keep financial reports, the marketer to promote the product and see the effectiveness of advertising, the manager — to plan the budget and monitor its implementation.
Download demo version
You can download a trial version of the software on the developer's website. Within two weeks it’ll be possible to assess the potential of the management program and decide to install the full version.
The management program automatically generates convenient and functional databases by category. They are updated constantly. The system keeps a database of visits, transport, employees. Photos scanned copies of documents can be attached to persons.
The management system handles large amounts of data without sacrificing performance. The necessary information on visitors, time, date, purpose of the visit, transport, goods shipped, an employee can be found in seconds by a simple search query for any time period. You can upload files of any format to the management program. Instructions to guards can be supplemented with diagrams, pictures, video files, audio recordings.
Management of checkpoints is automated. The system reads bar codes from passes, takes into account entry and exit, keeps track of compliance with labor discipline of the facility personnel, easily recognizes faces and compares them with photo data in databases, identifying people. The management program shows which types of protection activities at the facility are most common. If the greatest load falls on the checkpoint or the protection of the premises, then the head of the organization should be able to correctly balance the forces.
Order a facilities protection management
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

The program will be installed
If the program is purchased for 1 user, it will take no more than 1 hourBuy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!
Facilities protection management
The system from our developers shows the real state of work of the facility’s guards. At the end of the reporting period, the manager receives a report on the personal performance of each protection officer. This helps to make decision about bonuses or dismissals. The management program maintains financial statements — shows income, expenses in all areas, including protection activities. All documents, reports, payments, acts, and contracts are automatically drawn up by the management program, eliminating the possibility of errors and freeing people from an unpleasant paper routine.
The system unites in one info-space not only protection posts but also different departments of the facility, as well as its different branches. This gives employees the opportunity to communicate more quickly, and the manager to exercise management and management of all processes.
The software has a convenient built-in scheduler. It’ll help in planning any complexity. The facility’s management should be able to customize the frequency of reports. They’ll be able to get all the necessary information in the form of graphs, charts, and tables with comparative information for the previous period.
The management program is integrated with video cameras, facilitating the protection of the object, especially its cash registers, warehouses, and checkpoints. This program maintains expert warehouse records, shows the movement of goods, materials, raw materials. The data on the names to be displayed is sent to the guards immediately. An advanced management program integrates with the website and telephony, as well as with any trade and warehouse equipment and payment terminals.
The system from the USU Software development team has differentiated access. Employees should receive information that is appropriate for their level of competence. The economist won’t have access to information about the intricacies of the object of protection, and the guard won’t see information about the financial statements. The management program is very easy to use — it has a quick start, an intuitive interface, and everyone can handle it. This management system can conduct mass or personal distribution of information via SMS or e-mail.









