Operating system: Windows, Android, macOS
Group of programs: Business automation
Program for a checkpoint
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
Program screenshot
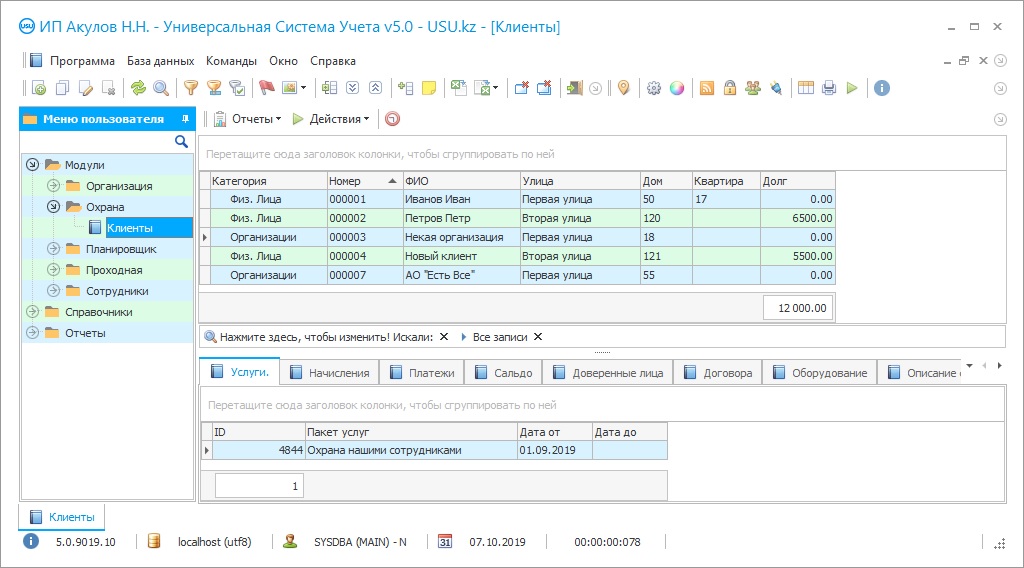
The checkpoint program is one of the configurations of the USU Software system, which allows organizing electronic control over the employees of the organization and visitors passing through the checkpoint - a system of turnstiles remotely controlled by a security officer or opened by scanning an access password that is assigned to an employee is in the form of a barcode on a checkpoint card, badge, pass - there are many names, the essence is the same - this is control over the checkpoint and exit, which is regulated by the checkpoint. The checkpoint program automatically performs many functions - it scans the barcode, compares the data with the employees and visitors available in the database, can carry out face-control on the photographs attached to the database, collects data on everyone who passed through the checkpoint - by name and with an indication time, filling in with this information the electronic log of visits and the worksheet of each employee. The participation of the person controlling the flow at the checkpoint in the program for the checkpoint is minimal - to enter their notes, comments, observations, remarks in electronic forms, in a word, everything that can be useful when specifying visits for the period. Most importantly, it is impossible to agree with the checkpoint program so as not to record being late or leaving the workplace at an inopportune hour, going on an extra smoke break, etc. - the procedure depends on the regime or internal rules of the enterprise.
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-05-03
Video of program for a checkpoint
This video can be viewed with subtitles in your own language.
The checkpoint program is installed on digital devices with the Windows operating system by employees of the USU Software, for this, they use remote access via an Internet connection, so no physical presence is required, which saves time for both parties. In general, the main task of the checkpoint program is to save working time and labor costs, based on which there is an increase in the efficiency of the enterprise even when performing one, but very important daily duty - control over the working time of personnel, which can be recorded, including at the checkpoint. The entrance program is not sick, thus, it does not need a paid sick leave, and it does not need to be replaced by anyone - it does its job day and night, feeling the need for only one thing - timely information about ‘passwords and attendances’ to compare and make a decision - allow the checkpoint to the visitor or refuse. The program makes a decision instantly - any of its operations, regardless of the amount of data in processing, is performed in fractions of a second, imperceptible to human perception, therefore they say that all accounting, control, and calculation procedures that are performed by the program automatically go in the current time mode.
Download demo version
Despite its ‘high-tech’ functionality, the program is available to all employees, no matter what computer skills they have - the program has a simple interface and easy navigation, which admits everyone to quickly master it without additional training, instead of which the developer conducts a short presentation remotely all its possibilities. If the enterprise has several entrances, the program forms a common information space - the activities of each checkpoint are recorded in a single database, the distribution of information is performed automatically by persons, services, work schedules, timesheets. The work of the controller is reduced to monitoring the process of entry exit, registration of visitors, removal of inventory items from the territory of the enterprise, and entering the data required by the program. The checkpoint program integrates with digital equipment, in particular, with a barcode scanner and CCTV cameras, which expands the capabilities of both sides and improves the quality of the checkpoint. In addition, the program generates by the end of the period many statistical and analytical reports on the access control - how many employees violate it, to what extent and with what regularity, whether all employees fulfill the amount of working time requirements depending on their work schedule, who delayed most often, and who never. Such information allows drawing up a disciplinary ‘portrait’ of personnel, better understanding the needs and demands on which labor productivity depends, and identifying those who do not meet corporate standards.
Order a program for a checkpoint
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

The program will be installed
If the program is purchased for 1 user, it will take no more than 1 hourBuy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!
Program for a checkpoint
The program helps to form a base of visitors, so as not to order a pass to enter every time for those who often come to the company on duty, and, even if the visitor is not a frequent visitor, the program saves data about the person, including a photo on the first visit, and automatically recognizes at the second. If employees of the checkpoint controlling different entrances enter their registration data at the same time, the program saves them without access conflicts, since it has a multi-user interface that eliminates these problems. The information in the program has conveniently structured processes, subjects, and objects format, which allows quickly using it when searching for information about any visitor or employee of the enterprise.
The program is designed to organize access control at a separate enterprise and in a business center, allows visually controlling the entrance and exit of each employee. Photos of visitors are saved in the corresponding database - they can be attached to personal files organized in the system for everyone who has received permission to enter. Attached to the same personal files are scanned copies of identity cards presented at the checkpoint, which the system quickly scans and saves, using further in control. The program instantly searches the entire history of any person's visits, keeps track of the time spent on the territory of the enterprise, and introduces sorting by the purpose of visits. Employees of the checkpoint work in personal electronic documents to limit the area of responsibility of each, the information they add to the system is marked with a login. Each user of the system receives an individual login and a password protecting it. They determine the amount of available service information to fulfill duties. The company's management carries out regular control over the electronic forms of users to check their compliance with the real state of affairs at the enterprise. An audit function is offered to assist the management, its task is to highlight new data and revised old values that have been added to speed up the procedure.
In addition to this function, the program automatically transfers a large number of values from external files into the system, which is important when visiting large groups. The transfer of personal data from the list of visitors with attached scanned copies of their documents allows forming a database, regulating this data general checkpoint. The reverse export function works in the program, with its help they export service materials to external files with automatic conversion to any required format. The program generates automatically the entire document flow of the enterprise, including any types of reporting, including accounting and statistical, all types of invoices. The program has a formed nomenclature, when taking out materials, it verifies the data with it and the invoice database to identify the goods, check the permission to take out. To keep track of visitors, their own database is formed in CRM format, which contains personal data, contacts, scans of documents, photos, history of visits by chronology. Employee's interaction between clarifications and confirmations is carried out through active messages that pop up in the corner of the screen, clicking on them gives a transition to the discussion.









