Operating system: Windows, Android, macOS
Group of programs: Business automation
Registration of visits
- Copyright protects the unique methods of business automation that are used in our programs.

Copyright - We are a verified software publisher. This is displayed in the operating system when running our programs and demo-versions.

Verified publisher - We work with organizations around the world from small businesses to large ones. Our company is included in the international register of companies and has an electronic trust mark.

Sign of trust
Quick transition.
What do you want to do now?
If you want to get acquainted with the program, the fastest way is to first watch the full video, and then download the free demo version and work with it yourself. If necessary, request a presentation from technical support or read the instructions.

Contact us here
How to buy the program?
View a screenshot of the program
Watch a video about the program
Download demo version
Compare configurations of the program
Calculate the cost of software
Calculate the cost of the cloud if you need a cloud server
Who is the developer?
Program screenshot
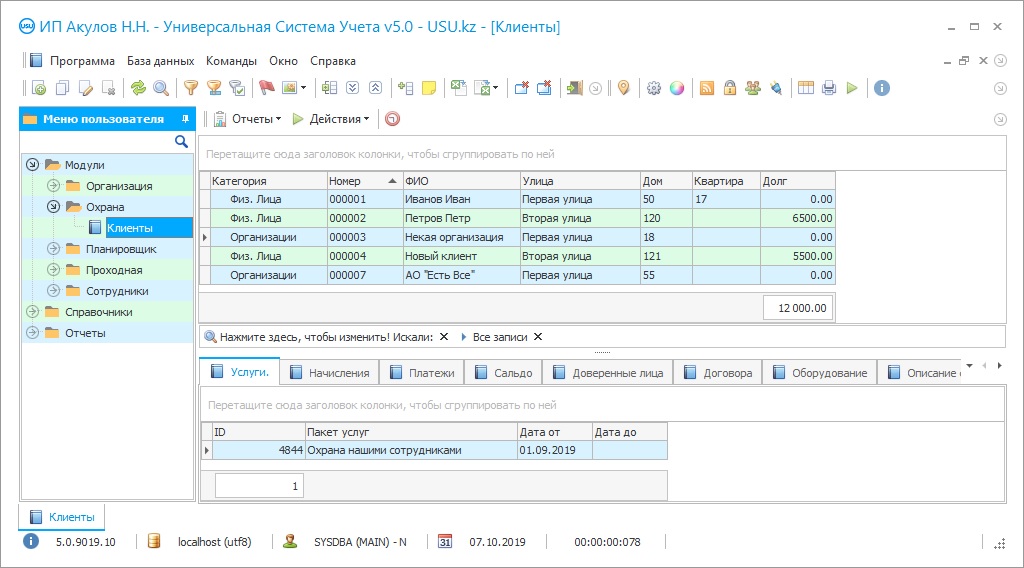
Registration of visits is necessary for each organization, the reception of visitors to which is carried out through a special checkpoint. Registration is necessary to have an idea of whether the staff is observing their shift schedule and whether they are late, and if they are outsiders, then how often and for what purpose they appear at your enterprise. The main purpose of maintaining the registration of visits is to record all visits and movements of employees on the territory of the company. This procedure is carried out manually if the security service independently records each visit to a special register. Also, you can organize the registration through an automated program, which makes this process quick and comfortable for all its participants. The second option has been quite popular in recent years since it significantly surpasses manual accounting in its qualities. This is since by entering records manually, you always run the risk of becoming dependent on external circumstances. A slightly increased load, or distracted attention, and the employee may already lose sight of something, not add or write it down incorrectly, which of course have a huge impact on the reliability of the final indicators and the quality of information processing. Unlike humans, a computer application works stably, uninterruptedly, and error-free under all circumstances, guaranteeing a high processing speed of data of any size. In addition, using paper samples of books and magazines, there always a risk of their loss or damage, which completely excludes automated complex that guarantees the safety and security of electronic information. Plus, the program implemented in the management of the organization has a huge impact on the direct work of the manager and staff, making it easier, more comfortable, and more productive. All thanks to the fact that modern technologies are able to take over most of the daily routine work of employees, allowing them to free themselves to solve the most important tasks in the security activities for which they are responsible. It is quite easy to achieve business automation because all that is required for this is to decide on the choice of an application that is suitable in terms of price and options. At the moment, this is not difficult to do, because modern developers present a huge selection of different software.
Who is the developer?

Akulov Nikolay
Expert and chief programmer who participated in the design and development of this software.
2024-05-10
Video of registration of visits
This video can be viewed with subtitles in your own language.
One of the applications that all owners and managers should definitely pay attention to is the USU Software system, which has been in demand for more than 8 years. The program has fairly extensive functionality that is optimal for visits' registration at the checkpoint. The fact is that registration platform manufacturers offer customers a choice of more than 20 different configurations, tailored specifically for different business segments and the nuances of their management. The conducting security activities module is just one of them. Even though it has a rather narrow specialization, using it you able not only to control visits but also to establish accounting of financial flows, personnel, storage facilities, planning, and CRM. Hence, we confidently say that USU Software is ready-made to manage all internal aspects of a business solution. In addition to such practicality, the product installation delight with its price and its availability. It is very easy to use and install and thus does not cause you any difficulties at one or the other stage. Installing and configuring a platform for a new user takes place remotely, which requires only your computer and an Internet connection. After this stage, you can start working immediately, even if you are an absolute beginner in the art of automated control. At first, the study of the interface helps you to conduct the built-in tooltips that guide the user like an electronic guide. Additionally, you can use the viewing of training videos posted on the USU Software website in the free access that does not require registration. The system interface has a lot of all kinds of customizable parameters and modes that optimize workflows and keep records of visits. You can find a complete list of tools in the introductory PDF presentation posted on the site. But one of the most important is the multi-user mode, thanks to which all employees of the company have the opportunity to work in the universal visits system simultaneously and together, freely exchanging data and files if necessary. To activate this mode, all users must connect to a single local network or the Internet, and it would also be rational to create each employee his account and issue a personal login and password. The ability to use different accounts allows delimiting the workspace, facilitating the registration of an employee in the database, tracking his activity during working hours, and also setting up information access boundaries to his office to protect confidential information from unnecessary views.
Download demo version
Registration of visits to the USU Software is quite simple. It is enough to install the system at the checkpoint of your establishment together with the registration procedure necessary equipment (scanner, web camera, video surveillance cameras). It is very convenient to use conducting registration of visitors bar-coding technology, which is used to mark the badges of staff members. Hence, to provide registration, an employee only needs to swipe his badge over the scanner built into the turnstile, and he automatically registered in the electronic database. It remains to solve the problem with temporary visitors who come for a limited time. To them, the security officers able to generate a temporary pass in a matter of minutes, which is created in the program according to a pre-prepared template. Moreover, you can even attach a photo taken there through a web camera. On such a pass, the date of its issue is also indicated, since it has a limited period. Carrying out the registration in this way, not a single visitor remains unrecorded in the database.
Order a registration of visits
To buy the program, just call or write to us. Our specialists will agree with you on the appropriate software configuration, prepare a contract and an invoice for payment.
How to buy the program?

The program will be installed
If the program is purchased for 1 user, it will take no more than 1 hourBuy a ready-made program
Also you can order custom software development
If you have special software requirements, order custom development. Then you won’t have to adapt to the program, but the program will be adjusted to your business processes!
Registration of visits
So, summing up the results of this essay, it follows that the universal registration system is the best registering visits computer software option at the access control of any enterprise. If you have any additional questions, we recommend that you contact our Skype specialists for a correspondence consultation, where they inform you in detail about all the advantages of using the platform installation.
In the ‘Reports’ section of the main menu, you can view all the visits to the company made during the selected period and analyze which clients you have more. In working with information about visits by workers of a work organization, you can check how they are observing the corresponding shift schedule. An unlimited number of employees working in different personal accounts can handle the registration of clients, which does not interfere with their joint activities. Using the analytical skills of the ‘Reports’ section, you can easily check how often your subordinates are late and can apply penalties. When issuing a temporary pass, the security service also records the purpose of the visit, which needed when compiling general statistics. Automated registration is quick and comfortable for both parties, without creating queues at the checkpoint. To record full-time employees, you can also engage in maintaining an additional questionnaire, which includes the parameters of his inspection: absence of alcoholic smell, conformity to appearance, etc. Most users also note the beauty and conciseness of the interface design style, which, moreover, comes with more than 50 design templates for every taste. The universal complex quickly and conveniently forms a database of contractors, where all records can be cataloged. You can organize the registration of visits and their maintenance within the framework of a unique application in any convenient language since it has a built-in language package. A quick start to work in the system is an indisputable advantage. You can set the displayed statistics on completed visits in the form of tables, graphs, diagrams, and various schemes, which is very convenient for visual perception. With the use of computer applications, it becomes much easier to organize various object's work schedules and delegate tasks to subordinates. Reconciliation and employee overtime payment now convenient, since all overtime and shortcomings to each of them are reflected in the application. The manager is able in a very short time to prepare a whole range of management reports that are generated in the program automatically in the ‘Reports’ section.









